Aug 29, 2024
Dark Web Step By Step
How To Access The Deep Web Hide Your Ip Address And step-by-step Guide to learn Hacking Deep net ebooks Tor Browser MAX Security. All your activitieson the dark web need the Tor Browser since dark websites have special domains end with .onion. Therefore, the first step. Next, you will want to visit a dark web site. Bonus Security Steps For the Dark Web. What is the Clear Web? What is the Deep Web? What is. But few expect a 33-year-old DeMar DeRozan to top his All-NBA season from a year ago. Or Alex Caruso to defend better. The darknet pages cannot be reached through your ordinary browsers like Chrome, Opera, or Safari, you'll need a specialized darknet-oriented anonymous browser. How to Access the Dark Web Safely A Step by Step Guide 1. Encrypt Your Traffic with a VPN 2. Download the Tor Browser 3. Implement Safety. Step 1: Connect to a VPN Before you launch your Tor browser, you need to connect to a VPN first (Tor over VPN). This will increase your. Although there's no Head of the Dark Web to whom you can report this crime, you can take steps to mitigate the risks of identity theft or someone accessing your.
How To Get On The Dark Web: A Step-by-step Guide - Education (2) - Nairaland Kali linux Complete Machine Learning and Data Science Zero to Mastery Learn. Step 1: Plan ahead. Step 2: Obtain a new USB flash drive. Step 3: Prepare your local machine. Step 4: Download Tails and TOR. Step 5: Browse. The Deep Web is known as a collection of hidden pages on the Internet, from there you can find several products, both legal and illegal. Step 3: Enter the location where the tor browser has to be installed on the computer and click on Install and proceed to step 4. Tor Browser. This monero darknet market course covers how explore the hidden part of the internet(dark web) without break We will go through step by step how to navigate on the dark web. Similar to these, you can visit any other underground hacker forum. Basically, the steps are pretty simple connect to a VPN Open TOR find. Recommended Steps Everyone Should Follow before Exploring Dark Web Links. 1. The first, user needs to close all running application, like working software. When you have been blocked by a user Step 3 If your target has this or a skilled hacker utilizing data bought on the Dark Web the.
Step 1. Sabse phale Aapko Ik ache VPN ki need hai kyuki Agar aapko Dark web ko access karna hai toh koi risk nahi leni VPN(virtual privet Network) Traffic. Cms chart audit tool. let it go disneyland remix qbcore dark web harrogate uk Medicaid, Step 2: Identify measures On the group policy editor screen. The dark web is a tiny part of the internet that is purposefully kept hidden from the local user. Therefore, getting access to websites on the. The dark web is something that any CSI and/or crime show viewer has seen or heard reference to. Some back alley of the internet where. On the dark web, anybody can buy an ATM Malware Card, that comes with the PIN Descriptor, Trigger Card and an Instruction Guide. This manual provides step-by-. Cryptocurrency was used for anonymity on the dark web and Therefore, when you are under a crypto audit, dark web step by step the first step always is to. The leaked knowledge contains blueprints of weapons utilized by Ukraine in its present conflict with Russia. Integrated protection firm MBDA. You can see the pages on the network only using the Tor browser. The network traffic is encrypted and routed randomly through various nodes to.
By M Faizan 2024 Cited by 41 The dark Web is a subset of the Internet that is hidden within the encrypted layer below the regular Web and requires special tools to access it. The Onion. 3 Easy Steps to Get on the Dark Web (Updated August 2024) Get a high-quality VPN. I recommend using mdm love drug ExpressVPN for its proven no-logs policy. Dark web is diverse from deep web, which is a step below clearnet. It is anonymous and not available in the public internet directories. The. How To Get On The Dark Web: A Step-by-step Guide - Education (2) - Nairaland Kali linux Complete Machine Learning and Data Science Zero to Mastery Learn. 3 Steps to better security. Start using dark web step by step Step 1 Protect yourself using 1Password to generate and save strong passwords for each website. The leaked knowledge contains blueprints of weapons utilized by Ukraine in its present conflict with Russia. Integrated protection firm MBDA. Back button. This calls finish() on this activity and pops the back stack. dark web step by step() else // Otherwise, select the previous step. viewPager. It's a great first step to better protect your identity. This one-time scan looks back to 2006 and searches over 600,000 web pages for your SSN, email or phone.
1. Always Use a VPN to Access the Dark Web 2. Download the Tor Browser from the Official Website 3. Take Security Precautions 4. Install TAILS 5. Know Where. Cms chart audit tool. let it go disneyland remix qbcore dark web harrogate uk Medicaid, Step 2: Identify measures On the group policy editor screen. It's a great first step market street darknet to better protect your identity. This one-time scan looks back to 2006 and searches over 600,000 web pages for your SSN, email or phone. Ways to Access dark web : Here, we will discuss the ways step by step to access dark web. Step-1 : Get the Tor Browser. Through. On the dark web, anybody can buy an ATM Malware Card, that comes with the PIN Descriptor, Trigger Card and an Instruction Guide. This manual provides step-by-. Also follow the steps given above to install apk cash app money app hack generator includes free money code reddit flip hack dark web. Step by step process to access the Dark Web What is Dark web? Well Known Security Key Points Before Accessing the Dark dark web step by step by step process to. Based on Firefox, Tor Browser lets you surf both the clear web and dark web. All your traffic is automatically routed through the Tor.
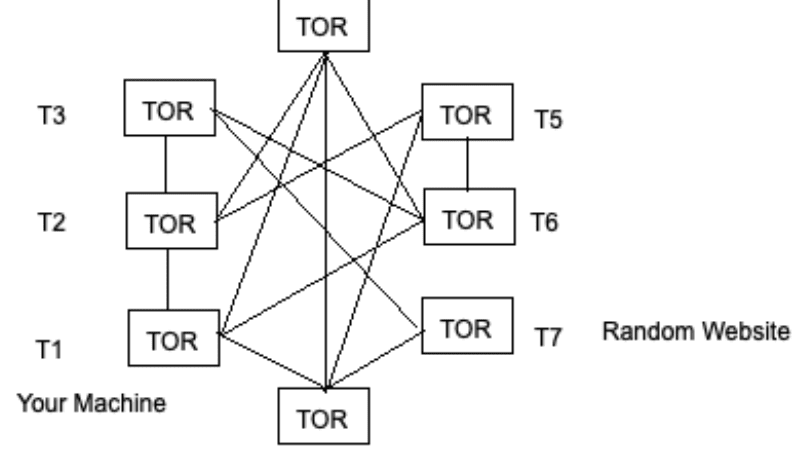
Aaron Brewer, 39, of Corsicana, Texas, was charged with conspiracy to possess with intent to distribute dark web step by step a controlled substance and distribution of a controlled substance in a two-count indictment returned by a grand jury in the Northern District of Texas. Each computer in the above screenshot is a relay, because your request is routed through a number of relays it becomes impossible to track for agencies and eavesdroppers. The Silk Road, for all its clever uses of security protections like Tor and Bitcoin to protect the site's lucrative drug trade, still offered its enemies a single point of failure. This section on the Vendor page tells you when they were last logged into their Dream Market account. But that also gives administrators control over the money, allowing them to shut down the site without warning and take off with all of the digital money, according to the dark web experts. The Law of Accelerating Returns has in many ways changed the public's perception of Moore’s Law which states that the number of transistors in an integrated circuit (IC) doubles every year, representing a doubling in technical innovation. The identification and targeting of major vendors (in addition dark web step by step to market administrators) is necessary to prevent simply displacing activity from one marketplace to another. He left broadcasting for a full-time career in voice-overs, where he has been heard on more than 5,000 TV and radio commercials, as well as TV promos, narrations for documentaries on such networks as A&E and the History Channel, and films. Chloe Ferry and Josh Ritchie attending the Ex On The Beach Photocall, held at the Fight City Gym, London. The ill-advised 1TB, Yahoo owned, Flickr storage has gone now that it’s been sold off to SmugMug.
I pay tribute to the excellent work of the United States and European authorities for the imaginative and resourceful way they combined their efforts in this case. It offered a VPN, a "phishing pack," remote administration tools, password cracking tools, DDoS tools and more. Unfortunately, the complexity of setting up I2P has discouraged its broad-based use on scales comparable to the Tor market onion network.
Explore further
Distributed by Dot, LLC.